Handle with care: customer trust can be fragile
Companies that luxuriate in customer trust are the envy of CEOs, customer experience execs and CMOs everywhere. Customer trust doesn’t spring up overnight and it can’t be bought by money alone. Instead, trust builds, layer upon layer, each time a customer engages favorably or exceptionally with his or her supplier, and deepens each time a genuine corporate commitment to customer care surfaces during interactions. (For example, Amazon has always re-shipped my orders that never arrived with no questions asked–even though I’m fairly certain it’s from delivery company mishaps.) Companies that not only deliver the goods–figuratively and literally– with no delay, no mistakes and no damage–and take decisive action if something does go wrong–get to bank both goodwill and a burgeoning level of customer trust that expands over time if the supplier continues to excel. Plus, customer trust and even intimacy can get supercharged by the execution of new, exciting website and mobile functionality, such as biometrics, beacons, location marketing, mass customization and, say, 3D screens.
The gradual deepening of customer trust levels can be understood more fully through the lens of website maturity over the past two decades. As companies created richer websites that fostered greater customer interaction, and provided some perceived value by the customer as a result of the exchange, customer trust often grew exponentially:
- Initial websites won trust largely through personalization and ecommerce. When websites moved beyond publishing static content, and began using explicit and implicit personalization to tailor their ecommerce offers to match customer preferences, customers started forming emotional attachments to their suppliers. Whether the supplier was a retailer, insurance company, bank or services company, etc.— consumers that trusted their suppliers would more willingly and confidently provide personal information, such as financial data, physical data, employer data, family data, and so forth in exchange for greater convenience, better pricing, personalized recommendations and offers, and ultimately, a better experience. And all of this was made possible because the customer experienced and believed in an umbrella of privacy and security that protected the engagement. (See Figure 1 below.)

Figure 1: Initial stage of B2C Customer Trust Cycle
- Advanced websites built customer intimacy. Over time, websites grew richer in sophistication, providing (behind the scenes) next-best-action recommendations to customers; offering customized products and services; and, seamlessly integrating chat and customer contact centers with websites. This level of service was possible because many trusted suppliers now had vast amounts of historical and derived data about each customer to draw upon. This cycle of “trusted data transformed into greater products, services and experiences” isn’t going to stop; some customers are probably already willing to release biometric data in return for specialty designed clothing or a more competitive health care plan. And why not? In exchange for private information, high value customers now receive highly prized, exclusive experiences that make them feel great (reinforcing the cycle). In many instances, customer trust has blossomed into a rock-solid belief that the supplier’s website is secure and trustworthy, while providing an unprecedented level of intimacy between the supplier and the customer. (See Figure 2 below.)
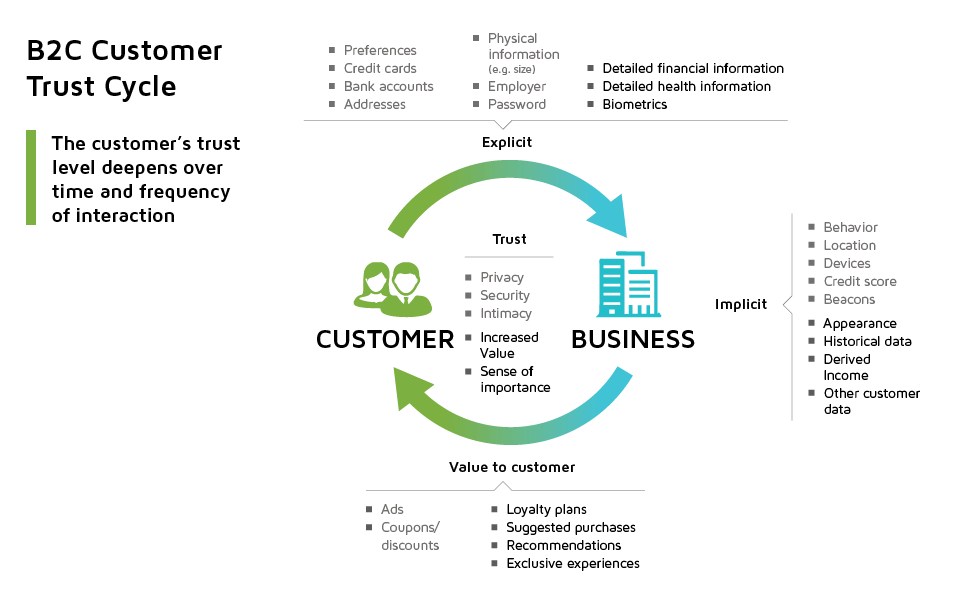
Figure 2: Deeper stage of B2C Customer Trust Cycle
(For an interesting take on the stages of web sites, see Kevin Cochrane’s “Interview: Three Waves of Digital Marketing”)
Now we get to the fragile part.
What if something happens to deeply damage the trusted relationship that forms between great suppliers and thrilled customers? All it takes is a rotten interaction with a horrible outcome to destroy all the goodwill the supplier has banked with its customer.
But other disasters can raze the goodwill in a few minutes, hours or day. For example:
- Security breaches shatter or severely damage customer trust. In fact, the customer’s sense of well-being and safety takes a meteor size hit whenever a security breach occurs. Breaches not only damage the targeted company; it clobbers all the customers who rely on that trusted relationship and willingly gave up their data in exchange for greater services, experiences and products. And it doesn’t even take a massive breach to create damage. Just having the corporate e-mail hacked and made public can create all sorts of havoc with customer confidence. While they may grit their teeth and continue doing business with the supplier, the trusted relationship usually becomes frayed and tattered. Breaches not only involve information theft or malicious intent, they also create a breach in customer trust. It may take years for the consumer to become comfortable again with the supplier and believe that their most private, confidential information is safe. And this insecurity will be even harder to overcome in the future should a problem occur, as websites continue to add more explicit and implicit data, such as visualization and derived information from cognitive computing. (See Figure 3.)
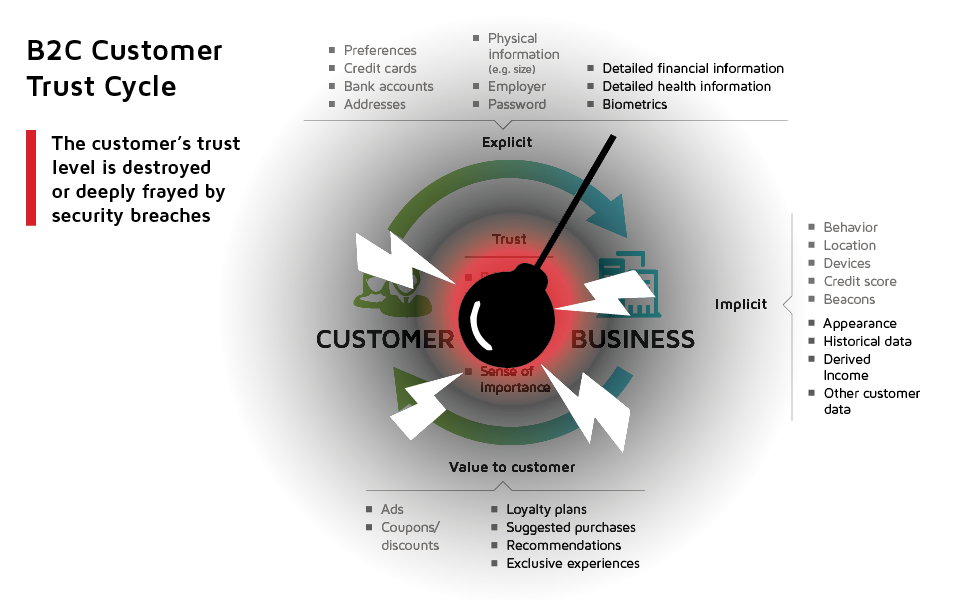
Figure 3: Breach in B2C Customer Trust Cycle
The potential threat to customer intimacy, privacy and trust is the urgent reason why CMOs and customer experience leaders must pay attention to cybersecurity measures before they happen–even if this seems pretty far afield for their expertise. The solutions for avoiding security breaches are not simple and easy to implement but the precautionary steps to take are straightforward and should be done in advance just in case those trusted customer relationships could be at risk:
- Start a conversation and then, a collaboration, between the CMO, CIO, chief risk officer and chief security officer identifying actions and responsibilities before a breach ever happens.
- Develop customer communication plans prior to any potential breach for how to approach customers and allay their fears.
- Create proactive processes and programs to educate and assist customers with safeguarding their information at all times.
- View and follow DoD as the thought leader in cybersecurity measures, using its practices and guidelines as best practice.
- Implement security precautions throughout the organization, with the goal of changing security risk behavior with every single employee.
- Consider next-gen cybersecurity measures, such as software defined perimeters, to thwart threats, keeping in mind that tighter security = harder to do business with.
These steps must be done because the customer relationship stakes are too high to endanger. The amount of private, personal, confidential data about customers–gathered painstakingly through years of website interactions–must be protected. Remember to handle those trusted relationships and confidential customer information with care–it can be fragile.